Salt Generate Keys For Minion
Posted By admin On 11.04.20- Salt Generate Keys For Minion Videos
- Salt Generate Keys For Minion Face
- Salt Generate Keys For Minion Youtube
- Salt Generate Keys For Minion 2017
- Salt Generate Keys For Minion Images
On the master side one can type $salt-key -f host. To check this is the correct fingerprint on the salt-minion side is not easy. It would be nice to have a command for the salt-minon side. For example /etc/init.d/salt-minion fingerprint or 'salt-minion-fingerprint'. Set a name to generate a keypair for use with salt -gen-keys-dir=GENKEYSDIR Set the directory to save the generated keypair. Only works with 'genkeysdir' option; default is the current directory.keysize=KEYSIZE Set the keysize for the generated key, only works with the '-gen-keys' option, the key size must be 2048 or higher, otherwise it will be rounded up to 2048. The default is 2048. Aug 11, 2017 Executing salt modules and states on minions is the normal way to interact with a minion, but sometimes it is a lot faster to manage a remote machine with a terminal shell over ssh. If that machine is behind a NAT, then it gets more difficult to ssh to that box, but if you control the salt master then you can setup a reverse SSH tunnel to the minion.
- SaltStack Tutorial
- SaltStack Useful Resources
- Selected Reading
Salt executes commands in a remote system by using salt-minion. This is the normal behavior. In some scenarios, the remote system can be accessed only by the SSH protocol. For these scenarios, Salt provides an option to connect the remote system using the SSH protocol only and execute the command through the SSH layer.
Salt SSH is very easy to configure. The only needed configuration is to specify the remote system details in a special file called as the Roster file. This roster file is normally located in /etc/salt/roster. The roster file will have all the information regarding the remote system and how can we connect to it. Once the roster files are configured, all the Salt commands are executed using the salt-ssh instead of the salt command.
Roster File
The Roster System is designed specifically for Salt SSH. This is designed as a pluggable system. The sole purpose of the roster system is to gather information about the remote system. The roster file is a YAML based configuration file containing remote system information as targets. These targets are a special data structure with a predefined set of attributes. A roster file contains one or more targets and each target is identified by a Salt ID.
The basic structure of the roster file is as follows −
All the other attributes supported by the roster file is optional. They are as follows −
port − SSH port number.
sudo − whether to run the command via sudo.
sudo_user − sudo user name.
tty − true if sudo is enabled.
priv − private key.
timeout − timeout for an SSH connection.
minion_opts − dictionary of minion opts.
thin_dir − target system's storage directory for salt components.
cmd_umask − umask to force for the salt-call command.
The sample roster file is as follows −
Deploy SSH Keys
Salt SSH will generate a default public/private key pairs for SSH logins. The default path will be /etc/salt/pki/master/ssh/salt-ssh.rsa. This key can be deployed to the remote system using the ssh-copy-id command as shown below.
Execute Command
Executing a salt command is as simple as changing the salt cli command into salt-ssh as shown below.
Raw Shell Command
Salt SSH provides an option (-r) to execute a raw command in the remote system bypassing the salt module and functions.
Targeting with Salt SSH
Targeting the remote system in Salt SSH supports only glob and regex targets. Since Salt SSH is a separate module, it provides only limited options as of now and will provide more features in the near future.
Starting Salt¶
Salt functions on a master/minion topology. A master server acts as acentral control bus for the clients, which are called minions. The minionsconnect back to the master.
Setting Up the Salt Master¶
Turning on the Salt Master is easy -- just turn it on! The default configurationis suitable for the vast majority of installations. The Salt Master can becontrolled by the local Linux/Unix service manager:
On Systemd based platforms (newer Debian, openSUSE, Fedora):
On Upstart based systems (Ubuntu, older Fedora/RHEL):
On SysV Init systems (Gentoo, older Debian etc.):
Alternatively, the Master can be started directly on the command-line:
The Salt Master can also be started in the foreground in debug mode, thusgreatly increasing the command output:
The Salt Master needs to bind to two TCP network ports on the system. These portsare 4505 and 4506. For more in depth information on firewalling these ports,the firewall tutorial is available here.
Finding the Salt Master¶
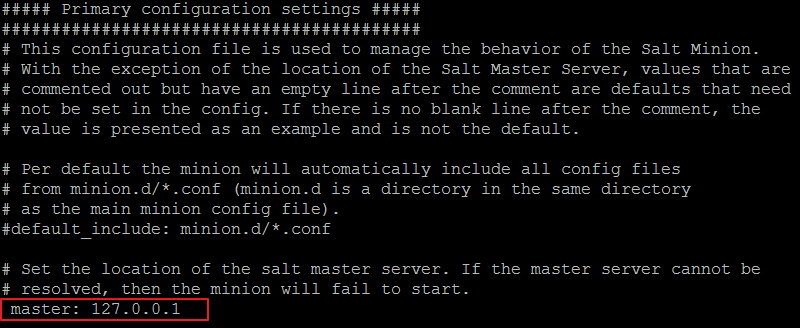
When a minion starts, by default it searches for a system that resolves to the salt hostname on the network.If found, the minion initiates the handshake and key authentication process with the Salt master.This means that the easiest configuration approach is to set internal DNS to resolve the name salt back to the Salt Master IP.
Otherwise, the minion configuration file will need to be edited so that theconfiguration option master points to the DNS name or the IP of the Salt Master:
Note
The default location of the configuration files is /etc/salt. Mostplatforms adhere to this convention, but platforms such as FreeBSD andMicrosoft Windows place this file in different locations.
/etc/salt/minion:
Setting up a Salt Minion¶
Note
The Salt Minion can operate with or without a Salt Master. This walk-throughassumes that the minion will be connected to the master, for information onhow to run a master-less minion please see the master-less quick-start guide:
Now that the master can be found, start the minion in the same way as themaster; with the platform init system or via the command line directly:
As a daemon:
In the foreground in debug mode:
When the minion is started, it will generate an id value, unless it hasbeen generated on a previous run and cached (in /etc/salt/minion_id bydefault). This is the name by which the minion will attemptto authenticate to the master. The following steps are attempted, in order totry to find a value that is not localhost:
The Python function
socket.getfqdn()is run/etc/hostnameis checked (non-Windows only)/etc/hosts(%WINDIR%system32driversetchostson Windows hosts) ischecked for hostnames that map to anything within 127.0.0.0/8.
If none of the above are able to produce an id which is not localhost, thena sorted list of IP addresses on the minion (excluding any within127.0.0.0/8) is inspected. The first publicly-routable IP address isused, if there is one. Otherwise, the first privately-routable IP address isused.
If all else fails, then localhost is used as a fallback.
Note
Overriding the id
The minion id can be manually specified using the idparameter in the minion config file. If this configuration value isspecified, it will override all other sources for the id.
Now that the minion is started, it will generate cryptographic keys and attemptto connect to the master. The next step is to venture back to the master serverand accept the new minion's public key.
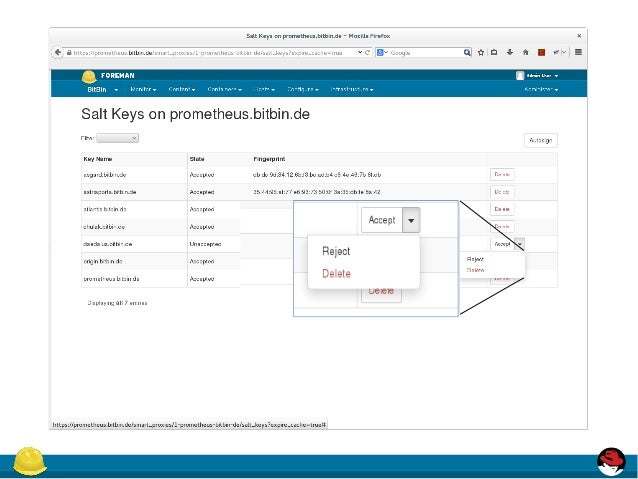
Using salt-key¶
Salt authenticates minions using public-key encryption and authentication. Fora minion to start accepting commands from the master, the minion keys need to beaccepted by the master.
The salt-key command is used to manage all of the keys on themaster. To list the keys that are on the master:
Salt Generate Keys For Minion Videos
The keys that have been rejected, accepted, and pending acceptance are listed.The easiest way to accept the minion key is to accept all pending keys:
Note
Keys should be verified! Print the master key fingerprint by running salt-key-Fmasteron the Salt master. Copy the master.pub fingerprint from the Local Keys section,and then set this value as the master_finger in the minion configurationfile. Restart the Salt minion.
On the master, run salt-key-fminion-id to print the fingerprint of theminion's public key that was received by the master. On the minion, runsalt-callkey.finger--local to print the fingerprint of the minion key.
On the master:
On the minion:
If they match, approve the key with salt-key-afoo.domain.com.
Sending the First Commands¶
Now that the minion is connected to the master and authenticated, the mastercan start to command the minion.
Salt commands allow for a vast set of functions to be executed and forspecific minions and groups of minions to be targeted for execution.
The salt command is comprised of command options, target specification,the function to execute, and arguments to the function.
A simple command tostart with looks like this:
The * is the target, which specifies all minions.
test.version tells the minion to run the test.version function.
In the case of test.version, test refers to a execution module. version refers to the version function contained in the aforementioned testmodule.
Note
Execution modules are the workhorses of Salt. They do the work on thesystem to perform various tasks, such as manipulating files and restartingservices.
The result of running this command will be the master instructing all of theminions to execute test.version in paralleland return the result. Using test.versionis a good way of confirming that a minion is connected, and reaffirm to the userthe salt version(s) they have installed on the minions.
Note
Each minion registers itself with a unique minion ID. This ID defaults tothe minion's hostname, but can be explicitly defined in the minion config aswell by using the id parameter.
Of course, there are hundreds of other modules that can be called just astest.version can. For example, the following would return disk usage on alltargeted minions:
Getting to Know the Functions¶
Salt comes with a vast library of functions available for execution, and Saltfunctions are self-documenting. To see what functions are available on theminions execute the sys.doc function:
The G Suite Single Sign-On service accepts public keys and certificates generated with either the RSA or DSA algorithm. To use the service, you need to generate the set of public and private keys and an X.509 certificate that contains the public key. Once you have a public key or certificate. To generate private (d,n) key using openssl you can use the following command: openssl genrsa -out private.pem 1024 To generate public (e,n) key from the private key using openssl you can use the following command: openssl rsa -in private.pem -out public.pem -pubout. Generating the Public Key - Windows 1. At the command prompt, type the following: openssl rsa -in rsa.private -out rsa.public -pubout -outform PEM 2. The public key is saved in a file named rsa.public located in the same folder. Generating the Private Key - Linux 1. Open the Terminal. Navigate to the folder with the ListManager directory.  That generates a 2048-bit RSA key pair, encrypts them with a password you provide and writes them to a file. You need to next extract the public key file. You will use this, for instance, on your web server to encrypt content so that it can only be read with the private key. Export the RSA Public Key to a File. This is a command that is. Openssl rsa -in private.pem -outform PEM -pubout -out public.pem.
That generates a 2048-bit RSA key pair, encrypts them with a password you provide and writes them to a file. You need to next extract the public key file. You will use this, for instance, on your web server to encrypt content so that it can only be read with the private key. Export the RSA Public Key to a File. This is a command that is. Openssl rsa -in private.pem -outform PEM -pubout -out public.pem.
This will display a very large list of available functions and documentation onthem.
Note
Module documentation is also available on the web.
These functions cover everything from shelling out to package management tomanipulating database servers. They comprise a powerful system management APIwhich is the backbone to Salt configuration management and many other aspectsof Salt.
Note
Salt comes with many plugin systems. The functions that are available viathe salt command are called Execution Modules.
Helpful Functions to Know¶
The cmd module containsfunctions to shell out on minions, such as cmd.run and cmd.run_all:
The pkg functions automatically map local system package managers to thesame salt functions. This means that pkg.install will install packages viayum on Red Hat based systems, apt on Debian systems, etc.:
Note
Some custom Linux spins and derivatives of other distributions are not properlydetected by Salt. If the above command returns an error message saying thatpkg.install is not available, then you may need to override the pkgprovider. This process is explained here.
The network.interfaces function willlist all interfaces on a minion, along with their IP addresses, netmasks, MACaddresses, etc:
Changing the Output Format¶
The default output format used for most Salt commands is called the nestedoutputter, but there are several other outputters that can be used to changethe way the output is displayed. For instance, the pprint outputter can beused to display the return data using Python's pprint module:
The full list of Salt outputters, as well as example output, can be foundhere.
salt-call¶
The examples so far have described running commands from the Master using thesalt command, but when troubleshooting it can be more beneficial to loginto the minion directly and use salt-call.
Doing so allows you to see the minion log messages specific to the command youare running (which are not part of the return data you see when running thecommand from the Master using salt), making it unnecessary to tail theminion log. More information on salt-call and how to use it can be foundhere.
Grains¶
Salt uses a system called Grains to build upstatic data about minions. This data includes information about the operatingsystem that is running, CPU architecture and much more. The grains system isused throughout Salt to deliver platform data to many components and to users.
Grains can also be statically set, this makes it easy to assign values tominions for grouping and managing.
A common practice is to assign grains to minions to specify what the role orroles a minion might be. These static grains can be set in the minionconfiguration file or via the grains.setvalfunction.
Targeting¶
Salt allows for minions to be targeted based on a wide range of criteria. Thedefault targeting system uses globular expressions to match minions, hence ifthere are minions named larry1, larry2, curly1, and curly2, aglob of larry* will match larry1 and larry2, and a glob of *1will match larry1 and curly1.
Many other targeting systems can be used other than globs, these systemsinclude:
Target using PCRE-compliant regular expressions
Target based on grains data:Targeting with Grains
Target based on pillar data:Targeting with Pillar
Target based on IP address/subnet/range
Create logic to target based on multiple targets:Targeting with Compound
Salt Generate Keys For Minion Face
Target with nodegroups:Targeting with Nodegroup
The concepts of targets are used on the command line with Salt, but alsofunction in many other areas as well, including the state system and thesystems used for ACLs and user permissions.
Salt Generate Keys For Minion Youtube
Passing in Arguments¶
Many of the functions available accept arguments which can be passed in onthe command line:
This example passes the argument vim to the pkg.install function. Sincemany functions can accept more complex input than just a string, the argumentsare parsed through YAML, allowing for more complex data to be sent on thecommand line:
Salt Generate Keys For Minion 2017
In this case Salt translates the string 'foo: bar' into the dictionary'{'foo': 'bar'}'
Note
Salt Generate Keys For Minion Images
Any line that contains a newline will not be parsed by YAML.