Cisco Crypto Key Generate Rsa Usage-keys
Posted By admin On 08.04.20- Cisco Crypto Key Gen Rsa
- Crypto Key Generate Rsa Command
- Cisco Crypto Key Generate Rsa Usage-keys Account
- Cisco Ios Crypto Key Generate Rsa
- Crypto Key Generate Rsa Command
- Cisco Crypto Key Generate Rsa Command
Aug 27, 2019 Procedure Step 1. Enables privileged EXEC mode. Enter your password if prompted. Enters global configuration mode. Specifies the RSA key pair to be used for SSH. A Cisco device can have many RSA key pairs. Enables the SSH server for. Crypto key generate rsa.cryptokeygeneratersa,page2 Cisco IOS Security Command Reference: Commands A to C, Cisco IOS XE Release 3SE (Cisco WLC 5700 Series). Cisco document says: crypto key generate rsa usage-keys general-keys key-pair-label general-keys (Optional) Specifies that the general-purpose key pair should be generated. Usage-keys (Optional) Specifies that two special-usage key pairs. Edit: this section appears to back up my claim that its related to naming the keypair. Without defining a hostname and domain name, you use the command 'ip ssh rsa keypair-name keypair-name ' and then 'crypto key generate rsa usage-keys label key-label modulus modulus-size '.
- October 2, 2015
- Posted by: Syed Shujaat
- Category: Cisco, Networking Solutions
Use this command to generate RSA key pairs for your Cisco device (such as a router). keys are generated in pairs–one public RSA key and one private RSA key.
If your router already has RSA keys when you issue this command, you will be warned and prompted to replace the existing keys with new keys.
NOTE: Before issuing this command, ensure that your router has a hostname and IP domain name configured (with the hostname and ipdomain-name commands).
Crypto key generate rsa. cryptokeygeneratersa,page2 Cisco IOS Security Command Reference: Commands A to C, Cisco IOS XE Release 3SE (Catalyst 3850 Switches). Dec 26, 2013 so it looks as if there is no point in the 'crypto key generate rsa' command if i follow it up with the 'crypto key generate rsa usage-keys label sshkeys mod 1024' command, i just wanted to make sure the first wasn't need for the second to work or something screwy like that. Facing ssh: connect to host port 22: Connection refused Issue on Cisco XR I have enabled ssh but still I face this issue when trying to login. I have generated key using #crypto key generate rsa usage-keys test. And after this enabled SSH v2. But still not able to login. Here is the output for ##show run i ssh.
You will be unable to complete the cryptokeygeneratersacommand without a hostname and IP domain name. (This situation is not true when you generate only a named key pair.)
Here are the steps to Enable SSH and Crypto Key setup : 2 config must requried for SSH
1 Setup Local VTY line User ID and password
router (Config) # Line VTY 0 15
router (Config-line)# login local
router (Config-line)# Exit
!!! create local login ID/Pass
router (Config)# username [loginid] password [cisco]
router (Config)# username loginid1 password cisco1
2. router (Config)# ip domain-name example.com
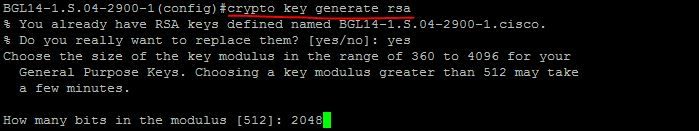
router (Config)# crypto key generate rsa
Cisco Crypto Key Gen Rsa
how many bits in the modulus [512] :1024
router (Config)# ip ssh version2
router (Config)# CTRL Z
Note | Secure Shell (SSH) may generate an additional RSA key pair if you generate a key pair on a router having no RSA keys. The additional key pair is used only by SSH and will have a name such as {router_FQDN }.server. For example, if a router name is “router1.cisco.com,” the key name is “router1.cisco.com.server.” |
Crypto Key Generate Rsa Command
This command is not saved in the router configuration; however, the RSA keys generated by this command are saved in the private configuration in NVRAM (which is never displayed to the user or backed up to another device) the next time the configuration is written to NVRAM.
Modulus Length
When you generate RSA keys, you will be prompted to enter a modulus length. The longer the modulus, the stronger the security. However, a longer modules take longer to generate (see the table below for sample times) and takes longer to use.
The size of Key Modulus range from 360 to 2048. Choosing modulus greater than 512 will take longer time.
| Router | 360 bits | 512 bits | 1024 bits | 2048 bits (maximum) |
|---|---|---|---|---|
| Cisco 2500 | 11 seconds | 20 seconds | 4 minutes, 38 seconds | More than 1 hour |
| Cisco 4700 | Less than 1 second | 1 second | 4 seconds | 50 seconds |
Cisco IOS software does not support a modulus greater than 4096 bits. A length of less than 512 bits is normally not recommended. In certain situations, the shorter modulus may not function properly with IKE, so we recommend using a minimum modulus of 2048 bits.
Syntax Description : Optional Strings to embed with SSH Crypto key
| general-keys | (Optional) Specifies that a general-purpose key pair will be generated, which is the default. | ||
| usage-keys | (Optional) Specifies that two RSA special-usage key pairs, one encryption pair and one signature pair, will be generated. | ||
| signature | (Optional) Specifies that the RSA public key generated will be a signature special usage key. | ||
| encryption | (Optional) Specifies that the RSA public key generated will be an encryption special usage key. | ||
| labelkey-label | (Optional) Specifies the name that is used for an RSA key pair when they are being exported.If a key label is not specified, the fully qualified domain name (FQDN) of the router is used. | ||
| exportable | (Optional) Specifies that the RSA key pair can be exported to another Cisco device, such as a router. | ||
| modulusmodulus-size | (Optional) Specifies the IP size of the key modulus.By default, the modulus of a certification authority (CA) key is 1024 bits. The recommended modulus for a CA key is 2048 bits. The range of a CA key modulus is from 350 to 4096 bits.
| ||
| storagedevicename: | (Optional) Specifies the key storage location. The name of the storage device is followed by a colon (:). | ||
| redundancy | (Optional) Specifies that the key should be synchronized to the standby CA. | ||
| ondevicename: | (Optional) Specifies that the RSA key pair will be created on the specified device, including a Universal Serial Bus (USB) token, local disk, or NVRAM. The name of the device is followed by a colon (:).Keys created on a USB token must be 2048 bits or less. |
| Command | Description |
|---|---|
| copy | Copies any file from a source to a destination, use the copy command in privileged EXEC mode. |
| cryptokeystorage | Sets the default storage location for RSA key pairs. |
| debugcryptoengine | Displays debug messages about crypto engines. |
| hostname | Specifies or modifies the hostname for the network server. |
| ipdomain-name | Defines a default domain name to complete unqualified hostnames (names without a dotted-decimal domain name). |
| showcryptokeymypubkeyrsa | Displays the RSA public keys of your router. |
| show crypto pki certificates | Displays information about your PKI certificate, certification authority, and any registration authority certificates. |
When trying to SSH to a Cisco Router or Switch you get this error
This can be caused by a number of reasons
Cisco Crypto Key Generate Rsa Usage-keys Account
- The transport setting on the vty lines is not permitting SSH
- You do not have SSH enabled
- An Access-List is blocking SSH traffic
Lets look at each scenario and enable the appropiate setting
For this tutorial I am using a Cisco CSR1000V as a test router running on my esxi server. This is a new install with no configuration.
First check the VTY lines with a simple show run and scroll to the bottom
Here you can see that for all VTY lines the transport input has been set to none – This means no connectivity!
Let fix that with one command
Now do a show run again and you will see transport input ssh on all lines
If we try to SSH to the router now it still fails
Jan 16, 2019 Adobe Photoshop CC Crack 2015 Product Key Full Free. Adobe Photoshop CC 2015 – a comprehensive solution for digital image professional, including the most advanced tools for working with photos and new opportunities for innovative ideas that can improve performance significantly.Edit photos with special precision, using intuitive new tools. Jul 02, 2015 Adobe Photoshop CC 2015 Crack Using it you are able to make quick image adjustments like those for removing chromatic aberrations, lens distortions and much more. One of the most incredible features of this program is the Content-Aware tools, designed to enable the users to remove content from a photo and replace it with a discreet patch. Adobe cc 2015 keygen. Adobe Premiere Pro CC 2017 v11.0 Crack Plus Serial Number. Download Crack Adobe Premiere Pro CC 2017 Full Version Crack Downlaod Adobe Premiere Pro CC 2017 v11.0 Crack is a.
So lets move to step 2 – enable SSH
If you run this command
It will show you what SSH is setup
Cisco Ios Crypto Key Generate Rsa
In this case none
R1# sh run inc ssh
R1#
So lets generate some SSH keys
This will fail as we have not specified a DNS name
Now run the crytpo command again and you will see SSH is enabled.
Lets try and SSH to our router again
Bingo!
We now have SSH access to our device
The final reason is an access list on vty lines – this can be checked at the first stage to see if there is any security blocking access.
Crypto Key Generate Rsa Command
I hope this helps!
Roger
Want to learn more about Network Automation?
Cisco Crypto Key Generate Rsa Command
Roger Perkin - CCIE #50038 is a Network Automation Engineer & CCIE Consultant based in the UK, currently working for Softcat Plc as a Senior Network & Security Consultant.
Rogers' CCIE Journey About Roger Contact Twitter Linkedin
